Aws Iot Device Management Secure Tunneling Greengrass
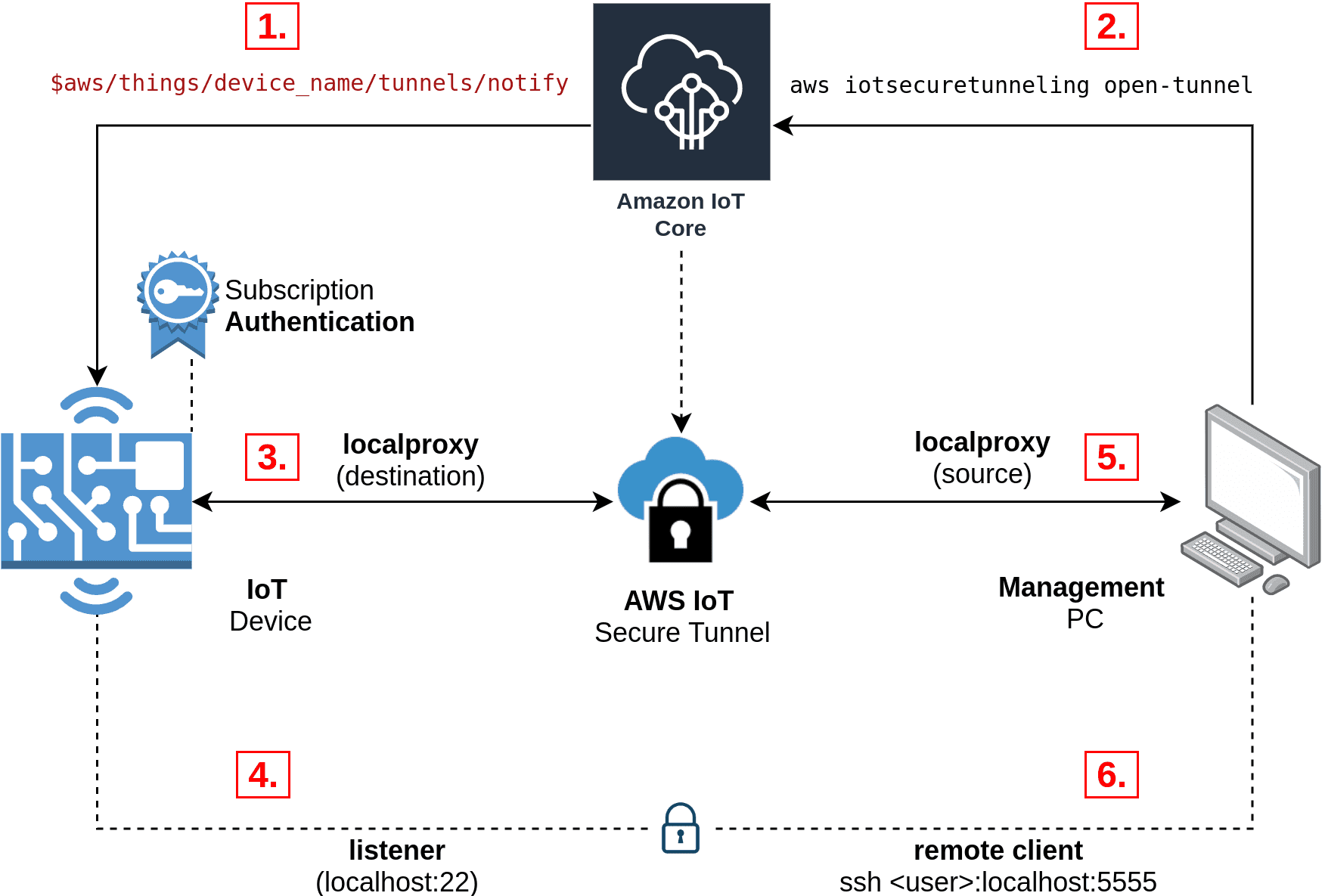
Use secure tunneling to establish bidirectional communication to remote devices over a secure connection that is managed by aws iot. Customers can troubleshoot misbehaving devices remotely to diagnose device issues, deploy a fix, and validate the device is working properly using remote shell or remote desktop operations. Secure tunneling does not require updates to your existing inbound firewall rules, so you can keep the same security level provided by firewall rules at a remote site.
Step by Step Introducing to AWS IoT Secure Tunneling and Pricing Details
In this blog you learned how aws iot secure tunnel can create a secure tunnel to your iot device (destination device) and carry out remote operations over ssh. Aws iot device management now enables customers to securely access remote devices using secure tunneling. The use case can be many, such as debugging or remedy device anomalies, and more.
You can connect to the destination device from your laptop or desktop computer as the source device by using the aws cloud.
Today we’re launching secure tunneling, a new feature in aws iot device management, which provides a secure remote access solution that directly integrates with aws iot to allow you to remotely access your iot devices from anywhere. Aws iot device management secure tunneling now provides support for multiple simultaneous tcp connections, unlocking new use cases for advanced troubleshooting on remote devices. Secure tunneling allows customers to establish bidirectional communication to remote devices using ssh, vnc or rdp. Aws iot secure tunneling helps customers establish bidirectional communication to remote devices that are behind a firewall over a secure connection managed by aws iot.
To demo aws iot secure tunneling, use our aws iot secure tunneling demo on github. Aws iot device management makes it easy to securely register, organize, monitor, and remotely manage iot devices at scale. In this video, you will learn how to use the secure tunneling For more information about how to use the aws management console to open a tunnel and start an ssh session, see open a tunnel and start ssh session to remote device.

The following video describes how secure tunneling works and walks you through the process of setting up an ssh session to a raspberry pi device.
Aws iot device management customers use secure tunneling to securely access and troubleshoot remote devices located behind a restricted firewall. Now, customers can make concurrent client connections to a single device over a secure tunnel using the new multiplexing capability. Device states can trigger specific device state lambda functions. セキュアトンネリングは、 aws iot device management の機能で aws iot が管理する安全な接続を介して、お客様がリモートデバイスにアクセスする仕組みを提供します。 secure tunneling は、既存のインバウンドファイアウォールルールの更新を必要としないため
This token will then be used by the local proxy application to create a websocket connection to the secure tunneling feature within aws iot device management. You have an iot device agent (see iot agent snippet) running on the remote device that connects to the aws iot device gateway and is configured with an mqtt topic subscription. For more information, see connect a device to the aws iot device gateway. By using device advisor, you can confirm that your devices can connect to aws iot core, follow security best practices and, if applicable, receive software updates from iot device management.

Try out this workshop to get started with aws iot using the aws iot device client.
It takes away the generic heavy lifting involved in connecting, managing, and securing your iot fleets, reducing the initial investment required for your iot The aws iot device client currently provides several docker images on various platforms and linux distributions. An iot application that connects to the aws iot device gateway and listens for new tunnel notifications over mqtt. For more information, see iot agent snippet.
A software proxy that runs on the source and destination devices and relays a data stream between secure tunneling and the device application. Aws iot secure tunneling allows customers to access devices that are deployed behind restricted firewalls at remote sites. When a tunnel is created, a pair of client access tokens (cat) will be generated and used by the source and destination devices to connect to the secure tunneling service. Secure tunneling is a feature of aws iot device management that helps customers accessing remote devices over a secure connection that is managed by aws iot.

Secure tunneling does not require updates to your existing inbound firewall rules, so you can keep the same security level provided by firewall rules at a remote site.
This is accomplished by a mutually initiated tunnel connection between source and destination devices that is brokered through the secure tunneling feature in aws iot device management. These secure device connections are authenticated and encrypted using transport layer security (tls). For example, if you use our registration workflow to register 10,000 devices, you would be charged for 10,000 devices registered. We are excited to announce that today we are reducing the price of the aws iot device management secure tunneling feature by 80%.
With the improved cost efficiencies, customers can now scale secure tunneling to access remote devices deployed behind restricted firewalls for troubleshooting, configuration updates, training, and other operational tasks for their growing iot workloads on aws. Quick and manual setup methods; Criteria quick setup manual setup; Create a new tunnel with default, editable configurations.